What is it?
Ransomware is cyber threat that uses cryptographic measures designed to extort money from users. They have been around for a number of years now in many variations such CryptoLocker or Torrentlocker. One of the newest is called ‘Satana’ which not only encrypts your files, but also the master boot record on the hard drive so Windows won’t boot! Another recent variation ‘WannaCry‘ also includes a worm (type of virus) that allows it to spread to other connected computers without any user interaction.
One of the earlier variations was the ‘Police virus’ or ‘FBI virus’ which would display an image on the screen of infected computers requesting the user to pay a certain amount in order to unlock the computer. This was supposedly due to illegal activity the user had done. No user files were affected and the infection was relatively easy to remove. The new versions of Ransomware take it to a new level as they hold your personal files to ransom.
What it does?
We will be discussing Cryptolocker as an example, but the process may vary slightly between the Ramsomware variations. It starts by typically arriving as an attachment from any number of supposedly legitimate companies & appears to be genuine. Once the user double clicks the file, the process begins. First step is that the malware saves the file to the user’s Windows profile and also adds a key to the registry file so it auto starts the next time you log in. It then starts itself twice in case the user tries to kill the process. Next step is for it to contact the malware’s server to obtain the RSA encryption key & then asymmetric encryption begins. Predetermined files are encrypted, anything from Word documents to family photos, emails and a myriad in between. These files are generally encrypted in alphabetical order.
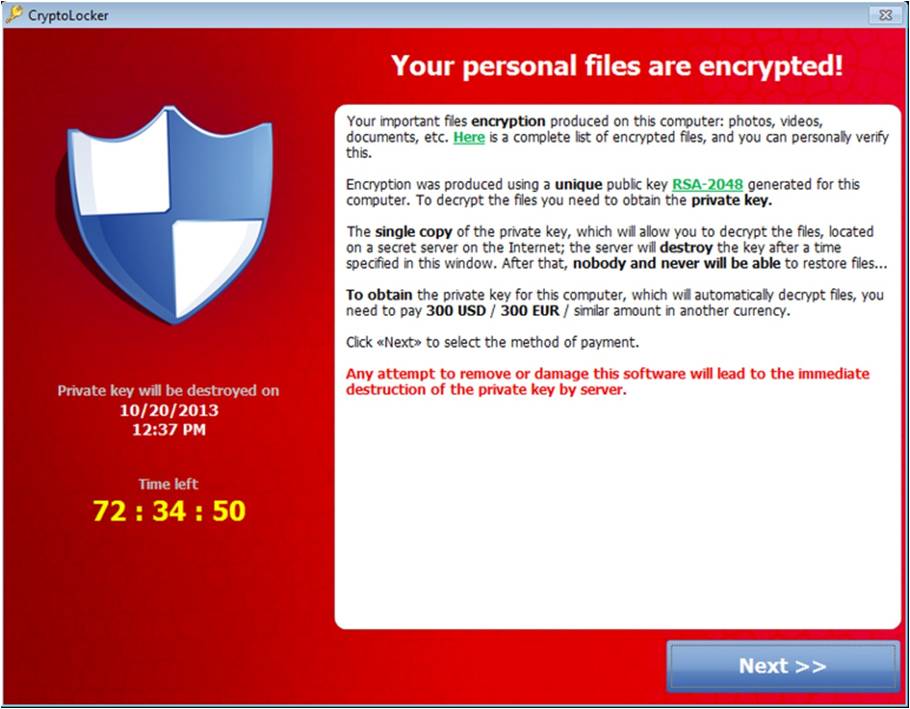
When finished, an image similar to this one is displayed.
Once this happens, there are a few options of how to proceed. First thing to do is remove the infection with reputable security software but that unfortunately still leaves your precious data encrypted. Without the decryption keys, your files are as good as gone so the next step is to recover the data from your most recent backup. You do have a recent backup, don’t you?
How to avoid it?
Ransomware is not that hard to avoid as long as you take a few precautionary measures. A little education for yourself and any team members you have goes a long way.
1. Don’t open attachments from unknown senders or anyone you suspect looks a little dodgy – use some vigilance.
2. Enable or show file extensions for known file types. By default, Windows hides the file extension for commonly used files (last three characters after the dot ie document.doc). This can be done quite easily in Windows. The malware is typically distributed as an .exe and masquerades to look like a pdf. With the extension hidden, you have no way of knowing the true file type.
3. Create & use a standard user account instead of an administrator account. This is an extra layer of protection to prevent software from installing as it’ll prompt you for the admin’s credentials in order to install anything.
4. Have current and up-to-date security software and updates for Windows. If you are running an unsupported operating system whilst connected to the internet (ie Windows XP) upgrading is essential as no future security patches will be released to fix found vulnerabilities. Doing this is a no brainer for anyone who wants to keep their system secure.
5. Have a consistent & reliable backup procedure in place, preferably offsite. Don’t just rely on an external HDD or cloud based storage (Dropbox, OneDrive, etc) as the malware has been known to encrypt files on those drives also. CKP Computers offers a cloud backup solution and are more than happy to discuss options.
6. Above all else, don’t pay the ransom! If you’ve taken the necessary precautions beforehand, it should never come to this point anyway.
I should point out too, if you suspect you’ve clicked something you shouldn’t have, immediately turn the computer off and leave it off and contact us for support. It takes time to encrypt the files on your system and chances are if you’ve acted quickly enough, only a small fraction of files (or hopefully none) have been affected.
For help with any of these steps, CKP Computers is here to help & keep you safe. Talk to us now for a no obligation discussion on your security needs. Our number is 0447 619 397 or you can send us an enquiry, either through our contact page, by Facebook or by email, helpme@ckpcomputers.com.au.